This problem is "I am a bot. My boss give me a key!" and a file 100.bin is given.
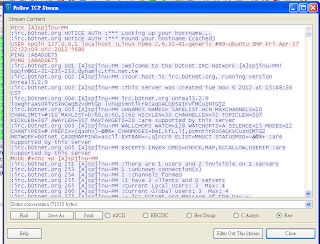
Although file command analysis this file as data, we can conclude this file is a pcap file by hex editor. So we can open this file by Wire Shark. After checking some packets, I find out some packet has use "PRIVMSG" command, which is IRC command. Therefor I follow TCP stream of those packet, and it is potential botnet traffic we need to analysis.
And observe this traffic, we can find a get command to 118.168.56.240
We first try to connect 118.168.56.240 directly, but it's fails. So we turn to find the traffic to 118.168.56.240 by wireshark. After selecting those packet and following TCP stream, we find the key in packet.


沒有留言:
張貼留言