With growth of cloud service , virtual machine become widely deployed. Nowadays, security issue was most concern when employ cloud service. Recently, Symantec has announced malware analysis report about Crisis. The most interesting thing is that Crisis can propagate though VMware, and this can be a good example of security issue of cloud service.
The only function demo by Crisis is copy it self into VM by VMware player tool. However with power of VMI technique proposed by many academic work, Mlaware can do almost everything from stealing information, killing Anti-Virus to invoking new process outside the VM. Due to this "out-of-box" character, system inside VM has no direct way to detect this kind of attack.
To raise this kind of attack, hacker should first get control of VMM. This can be done by misconfiguration of VM server, by insider attack, or some vulnerability of VM system(like vulnerability in Xen driver). Although attack to VM server is not an easy job, it still introduce a new attack vector that worthy to research in the future.
[1] Symantec Crisis Analysis Report
2012年8月28日 星期二
2012年8月23日 星期四
Introduction Virtualization in ARM platform
With explosion growth of mobile device, profits by attack mobile device also increase in an incredible rate. In some aspect, mobile combine to user even more close. Due to those reason, mobile malware appear exponentially. Especially for android malware due to it's widely used and open architecture. Many recent report also show that android malware increase exponentially, like Dissecting Android Malware: Characterization and Evolution in S&P'12 and F-secure Mobile Threat Report.
To address rapidly raise of mobile , both static and dynamic approach have been proposed. However static analysis suffer from code obfuscation and packed. In additional, static analysis will fail to reveal dynamic behavior include dynamic loading. Therefore dynamic analysis become standard and future trend to analysis android malware.
Although dynamic analysis can overcome code obfuscation and dynamic loading, dynamic analysis also has some shortcoming, like code coverage. In android platform, it lacks robust emulator that can precisely emulate common device like GPS, SMS and phone call, Some of which are most interesting when analysis android malware. However directly use real device to analysis is unavailable due to damage of read device and hard to scale. One reasonable solution is to use virtualization technique, however there are no stable virtualiazation platform in arm due to property of ARM system which not support virtualization.
Following the trend of virtualization, Sangsong proposed XEN/ARM and Columbia University also proposed KVM/ARM in 2010. However both solution lack of hardware support and have appendant memory and CPU overhead. In SOSP'11, Columbia University Department of Computer Science announce Cells project, which is the very first work about OS virtualization in ARM. Cells can leverage device that already support by OS without port every device. In Taiwan , SS Lab in NTHU also research in virtualization in ARM.Those research expose a new possibility for android malware analysis which employs real device with virtualization, so that we can reuse and reconstruct clean environment for analysis.
To address rapidly raise of mobile , both static and dynamic approach have been proposed. However static analysis suffer from code obfuscation and packed. In additional, static analysis will fail to reveal dynamic behavior include dynamic loading. Therefore dynamic analysis become standard and future trend to analysis android malware.
Although dynamic analysis can overcome code obfuscation and dynamic loading, dynamic analysis also has some shortcoming, like code coverage. In android platform, it lacks robust emulator that can precisely emulate common device like GPS, SMS and phone call, Some of which are most interesting when analysis android malware. However directly use real device to analysis is unavailable due to damage of read device and hard to scale. One reasonable solution is to use virtualization technique, however there are no stable virtualiazation platform in arm due to property of ARM system which not support virtualization.
Following the trend of virtualization, Sangsong proposed XEN/ARM and Columbia University also proposed KVM/ARM in 2010. However both solution lack of hardware support and have appendant memory and CPU overhead. In SOSP'11, Columbia University Department of Computer Science announce Cells project, which is the very first work about OS virtualization in ARM. Cells can leverage device that already support by OS without port every device. In Taiwan , SS Lab in NTHU also research in virtualization in ARM.Those research expose a new possibility for android malware analysis which employs real device with virtualization, so that we can reuse and reconstruct clean environment for analysis.
2012年8月14日 星期二
S&P'12 : ReDeBug: Finding Unpatched Code Clones in Entire OS Distributions
To deal with unpatched code clones in scale of OS-distribution, Jiyong Jang, Abeer Agrawal, and David Brumley from Carnegie Mellon University published "ReDeBug: Finding Unpatched Code Clones in Entire OS Distributions" in S&'P12, in which paper they proposed a system that can find unpatched code clones in OS distribution.
Due to the complexity of OS, there are always bugs inside whole system. Nowadays, patch is the standard methodology to update OS and fix bugs discovered. However there are still bugs produced by clone original buggy code in different sub-system, those bugs has the same attribute to original bug but hard to discover.
Most previous work like MOSS, CCFinder are focus on detection all code clone in system, which is limit by code scale. Many of them are language-dependent which is not suitable for OS ,which is multi-language environment.
In addition to find more unpatched buggy clone code, this paper try to answer following question.
Due to the complexity of OS, there are always bugs inside whole system. Nowadays, patch is the standard methodology to update OS and fix bugs discovered. However there are still bugs produced by clone original buggy code in different sub-system, those bugs has the same attribute to original bug but hard to discover.
Most previous work like MOSS, CCFinder are focus on detection all code clone in system, which is limit by code scale. Many of them are language-dependent which is not suitable for OS ,which is multi-language environment.
In addition to find more unpatched buggy clone code, this paper try to answer following question.
- how much (potentially) vulnerable code can an attacker identify when a patch is released
- how responsive is the new version of an OS to known security vulnerabilities
- how many persisting unpatched code clones
Due to the huge scale of OS, ReDeBug system proposed must has flexible scalability, Language agnostic, and has Lower false detection rate. ReDeBug
The flowchart above describe the progress of ReDebug.
- Pre-process the source
1. Performs normalization and tokenization
2. Moves an n-length window over the token stream. For each window, the resulting n-tokens are hashed into a Bloom filte
3. Stores the Bloom filter for each source file in a raw data format - Check for unpatched code copies
1. Extracts the original code snippet and the c tokens of context information from the pre-patch source
2. Normalizes and tokenizes the extracted original buggy code snippets
3. Hashes the n-token window into a set of hashes
4. Bloom filter set membership test - Post-process the reported clones
1. Performs an exact-matching test
2. Excludes dead code
3. reports only non-dead code to the user
2012年8月13日 星期一
S&P'12 : A Framework to Eliminate Backdoors from Response-Computable Authentication
This paper "A Framework to Eliminate Backdoors from Response-Computable Authentication" is published in S&P'12.The authors are Shuaifu Dai, Tao Wei, Chao Zhang, Tielei Wang, Yu Ding, Zhenkai Liang, Wei Zou from Peking University, University of California, Georgia Institute of Technology School of Computing, and National University of Singapore.
Standard authentication mechanism can be divide into two type. In first type use challenge and response mechanism and direct compare user response and respected response .This mechanism is widely employed in security system. For example, simple password checking, RC4. Second type feed user response to some authentication mechanism to check if authentication success. This paper focus on eliminate these backdoor based on previous authentication type, response-computable authentication (RCA).
//how about move authentication type to type 2.
To gain the control of system and against authentication mechanism, it is common for hacker to plaint backdoor into system. For examples VSFTPD 2.3.4 Backdoor in 2011, Back Door in Commercial Shopping Cart. Typically, backdoor can be classify to three types. Adversary model of backdoor is described following. The attacker has chance to modify develop progress but cannot interfere deployment environment. For examples, attacker may modify source code/binary directly, Thompson’s compiler backdoor[1], design to use weak cryptography algorithms. In this paper's 3 assumptions, 1) attacker cannot intercept code review and testing process.2) operating system is trusted. 3) password database is trusted.
Backdoor of RCA can be classify to two type, type T1 and type T2. In type T1, bypass response comparison, backdoor bypass comparison between user response and respected response according to user input(U-trigger backdoor), global states(G-trigger backdoor) and internal states(I-trigger backdoor). Type T2 backdoor, controlling computation of expected response, can furthermore divide to two type, type T2a and type T2b. Type T2a backdoor's response computation depends on information other than challenge and password. Type 2b is response computation collision-based backdoor.
Standard authentication mechanism can be divide into two type. In first type use challenge and response mechanism and direct compare user response and respected response .This mechanism is widely employed in security system. For example, simple password checking, RC4. Second type feed user response to some authentication mechanism to check if authentication success. This paper focus on eliminate these backdoor based on previous authentication type, response-computable authentication (RCA).
//how about move authentication type to type 2.
To gain the control of system and against authentication mechanism, it is common for hacker to plaint backdoor into system. For examples VSFTPD 2.3.4 Backdoor in 2011, Back Door in Commercial Shopping Cart. Typically, backdoor can be classify to three types. Adversary model of backdoor is described following. The attacker has chance to modify develop progress but cannot interfere deployment environment. For examples, attacker may modify source code/binary directly, Thompson’s compiler backdoor[1], design to use weak cryptography algorithms. In this paper's 3 assumptions, 1) attacker cannot intercept code review and testing process.2) operating system is trusted. 3) password database is trusted.
Backdoor of RCA can be classify to two type, type T1 and type T2. In type T1, bypass response comparison, backdoor bypass comparison between user response and respected response according to user input(U-trigger backdoor), global states(G-trigger backdoor) and internal states(I-trigger backdoor). Type T2 backdoor, controlling computation of expected response, can furthermore divide to two type, type T2a and type T2b. Type T2a backdoor's response computation depends on information other than challenge and password. Type 2b is response computation collision-based backdoor.
This framework eliminate backdoor by following steps.
- Explicit response comparison, this step divide verification process into response computation and response comparison. And ensure that only task response comparison do is comparing user response and respect response. This step can eliminate T1 backdoor.
- Function purification, this step ensure the only two factor involve in response computation is challenge and password. To make response computation a pure function(that is a function without side effects and deterministic), NaPu components employ a function level sandbox with global state isolation and iternel state reset. After this step T2a backdoors are eliminated.
- Backdoor usability testing, this step use collision testing to find out high collision algorithms and eliminated T2b backdoors.
- K. Thompson. Reflections on trusting trust. Communi- cations of the ACM, 27(8):761–763, 1984.
S&P'12 : Safe Loading - A Foundation for Secure Execution of Untrusted Programs
"Safe Loading - A Foundation for Secure Execution of Untrusted Programs" is the paper publish in S&P'12. Paper authors are Mathias Payer,Tobias Hartmann and Thomas R. Gross ,from ETH Zurich, Switzerland ETH.
There are many sanbox system employ BT(binary translation) to instrument application's system call. Libdetox, Vx32, Strata all belong to this type. To make decision if the program can be executed, research about policy-based system call authorization have been published. Moreover , full system virtualization, system call interposition also can isolate application.
This paper proposes a system to solve two problem that current SFI(software-based fault isolation) frameworks have. First is that sanbox can be attacked through dynamic loader.The second is that application inside sanbox must have privilege to map code into memory.
First problem presents due to complexity of loader. Current standard loader employ many functionality like debugging and call tracing. Exploiting bug of loader , privilege escape can be achieve with SUID program.
Secondary, the standard loader is responsible to map code include BT itself to memory which leaks information about BT. In addition, sanbox has no information about executable and data layout in memory.
In order to solve these two problems , this paper proposed SFI framework that replace standard loader by a lightweight secure loader and move secure loader into sandbox. Sandbox divide application into two domain, sandbox domain(secure loader and sandbox) and application domain. In sandbox domain, it can ensure only checked code loaded. Every applications run in application domain must be examined first and indirect control flow transfer will be checked by sandbox domain.
This framework have following three benefits:
There are many sanbox system employ BT(binary translation) to instrument application's system call. Libdetox, Vx32, Strata all belong to this type. To make decision if the program can be executed, research about policy-based system call authorization have been published. Moreover , full system virtualization, system call interposition also can isolate application.
This paper proposes a system to solve two problem that current SFI(software-based fault isolation) frameworks have. First is that sanbox can be attacked through dynamic loader.The second is that application inside sanbox must have privilege to map code into memory.
First problem presents due to complexity of loader. Current standard loader employ many functionality like debugging and call tracing. Exploiting bug of loader , privilege escape can be achieve with SUID program.
Secondary, the standard loader is responsible to map code include BT itself to memory which leaks information about BT. In addition, sanbox has no information about executable and data layout in memory.
In order to solve these two problems , this paper proposed SFI framework that replace standard loader by a lightweight secure loader and move secure loader into sandbox. Sandbox divide application into two domain, sandbox domain(secure loader and sandbox) and application domain. In sandbox domain, it can ensure only checked code loaded. Every applications run in application domain must be examined first and indirect control flow transfer will be checked by sandbox domain.
This framework have following three benefits:
- Restricting Privilege Escalation Attack
The light-weight loader will not suffer from complexity of standard loader.Without feature like debugging, backwards compatibility, secure loader only need to relocate code and thus reduce attack vector. - Protecting All Executed Application Code
All code run in application domain must use well-define API communicating to sandbox domain which can reduce attacker gathering information about loader. - Opening the Loader Black Box
With information shared by loader, sandbox can distinguish code region and data region.Therefore sandbox can provide trusted execution.
2012年8月12日 星期日
HIT2012 Wargame Writeup : Binary 7
This is Binary 1 writeup in HITCON 2012. Binary1 is the easiest binary problem. This problem give an executable and make you read the key.
It is easy to use IDA pro to inspect program flow which create 10 thread and write something to file "key.txt". So it is easy to guess that content wrote in "key.txt" is the answer.
There are decompile code that each thread.
Those threads sleep some times of a random number then print some characters to file.But without give rand function a seed, all random number produced in each thread is the same.So we can easily sort the characters in each thread by there sleep and get the key.
It is easy to use IDA pro to inspect program flow which create 10 thread and write something to file "key.txt". So it is easy to guess that content wrote in "key.txt" is the answer.
 |
| Flow of t100.exe |
Those threads sleep some times of a random number then print some characters to file.But without give rand function a seed, all random number produced in each thread is the same.So we can easily sort the characters in each thread by there sleep and get the key.
2012年8月10日 星期五
Hook CreateFile by pydbg
For malware analysis , file access is an
important factor to understand what malware do. Therefore in this article, I
write a small program that can hook windows createfile API.
TOOL
I use pydbg to develop this
program. pydbg is an subproject of paimei which is a well-known
reverse engineering tool.
It is not easy to install pydbg. During
installing pydbg, I have encountered following error, and there are some
articles solve those problems.
1.
pydasm not found
Because
pydbg need a decompiler, so we need to install pydasm first. Pydasm source can
be found here. https://code.google.com/p/libdasm/.
Then remove pydasm.pyd in pydbg source.
2.
unable to find vcvarsall.bat
This is due to lower version of VS compiler. We can solve this
problem by install higher version of VS or use mingw instead.
3. gcc:
error: unrecognized command line option '-mno-cygwin'
Option '-mno-cygwin' has been removed in gcc options.So we just remove '-mno-cygwin'
in ‘distutils\cygwinccompiler.py’
program review
Due to dynamic link of createfile API, we
cannot resolve address of createfile at program start. Therefore we need to hook
createfile API once kernel32.dll loaded.
We write a call back function load_dll () which
is triggered when dll load. And we use dbg.set_callback(LOAD_DLL_DEBUG_EVENT,
load_dll) to register callback of DLL loading. In function load_dll (), we
should check if kernel32.dll was loaded and hook createfile API(CreateFileW) .
file_hook.py
from pydbg import *
from pydbg.defines import *
import utils
import sys
import os
from ctypes import *
is_hook = 0
def FileCreateHook( dbg, args ):
buffer = ""
offset = 0
while 1:
byte = dbg.read_process_memory( args[0] + offset, 2 )
if not ( ord(byte[0])==0 and ord(byte[1])==0) :
buffer += byte
offset += 2
continue
else:
break
print unicode(buffer,"utf-16")
return DBG_CONTINUE
########################################################################################################################
def load_dll (pydbg):
last_dll = pydbg.system_dlls[-1]
print "loading:%s into:%08x size:%d" % (last_dll.name, last_dll.base, last_dll.size)
global is_hook
if is_hook==0 :
global hooks
hooks = utils.hook_container()
hook_address = pydbg.func_resolve_debuggee("kernel32.dll","CreateFileW")
print hook_address
if hook_address:
res = hooks.add( pydbg, hook_address, 7, FileCreateHook, None)
is_hook =1
print res
print "[*] CreateFileW hooked at: 0x%08x" % hook_address
else:
print "[*] Error: Couldn't resolve hook address."
return DBG_CONTINUE
dbg = pydbg()
dbg.set_callback(LOAD_DLL_DEBUG_EVENT, load_dll)
dbg.load(sys.argv[1])
is_hook =0
hooks=None
dbg.debug_event_loop()
reference
2012年8月6日 星期一
Malware Analysis : Trojan:AutoIt/Ransom.F
This malware has free sample and analysis report in malware.lu. So I try to analysis this sample as practice.
When I am analyzing this sample , it had detection rate 14/40 at VirusTotal
This malware come with icon as following image , which give us hint that this malware is compiled by AutoIt :
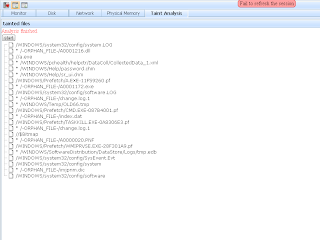
After this sample execution , it will connect to 95.163.104.88 which website was already removed.And this network activity can be cached by our tool. So we can observe that it connect to 95.163.104.88/spielberg/start.php.
We can also observe it change some file in following image:
When I am analyzing this sample , it had detection rate 14/40 at VirusTotal
This malware come with icon as following image , which give us hint that this malware is compiled by AutoIt :
After this sample execution , it will connect to 95.163.104.88 which website was already removed.And this network activity can be cached by our tool. So we can observe that it connect to 95.163.104.88/spielberg/start.php.
Sometimes there is an pop-up windows during execution :
This malware are packed by UPX. We can easily unpacked it and get origin executable.
The most interesting part is at end of script , it install some registry to trigger itself after booting.But this behavior is not detect by our tool. Then it check if explore.exe and taskmgr.exe existed to ensure it's GUI in top of windows.
This sample can not run by both anubis and cwsanbox.
2012年8月2日 星期四
WDK Minifilter Driver
In order to develop a driver for lab project , I try to review code in WDK source. After a very short view , I found there are some example code which are worthy to read.For example, In source code of Minifilter Driver(scanner.c), the author state that "This filter scans the data in a file before allowing an open to proceed. This is similar to what virus checkers do."
Minifilter can ....
To use Minifilter , first we need to construct a FLT_REGISTRATION structure.Here is examples in WDK.
const FLT_REGISTRATION FilterRegistration = {
sizeof( FLT_REGISTRATION ), // Size
FLT_REGISTRATION_VERSION, // Version
0, // Flags
ContextRegistration, // Context Registration.
Callbacks, // Operation callbacks
ScannerUnload, // FilterUnload
ScannerInstanceSetup, // InstanceSetup
ScannerQueryTeardown, // InstanceQueryTeardown
NULL, // InstanceTeardownStart
NULL, // InstanceTeardownComplete
NULL, // GenerateFileName
NULL, // GenerateDestinationFileName
NULL // NormalizeNameComponent
};
Third member of FLT_REGISTRATION is an FLT_CONTEXT_REGISTRATION which define context type. And Callbacks is an FLT_OPERATION_REGISTRATION structure to register call back operator.Following is examples of this two structure.
const FLT_CONTEXT_REGISTRATION ContextRegistration[] = {
{ FLT_STREAMHANDLE_CONTEXT,
0,
NULL,
sizeof(SCANNER_STREAM_HANDLE_CONTEXT),
'chBS' },
{ FLT_CONTEXT_END }
};
[structure explain]
const FLT_OPERATION_REGISTRATION Callbacks[] = {
{ IRP_MJ_CREATE,
0,
ScannerPreCreate,
ScannerPostCreate},
{ IRP_MJ_CLEANUP,
0,
ScannerPreCleanup,
NULL},
{ IRP_MJ_WRITE,
0,
ScannerPreWrite,
NULL},
{ IRP_MJ_OPERATION_END}
};
[structure explain]
The most interesting part is ScannerPostCreate function.Then we move to ScannerPostCreate function and take a look.
This function check file extension then call ScannerpScanFileInUserMode function. If the return value safe, then we leave it for write check.Otherwise , use FltCancelFileOpen to cancel file open operator.
In function ScannerpScanFileInUserMode , it calls FltReadFile function to read file content to buffer then pass it to user space by FltSendMessage.And user space program is responsible for scanning the content.
[How to communicate between user space and kernel space]
Minifilter can ....
To use Minifilter , first we need to construct a FLT_REGISTRATION structure.Here is examples in WDK.
const FLT_REGISTRATION FilterRegistration = {
sizeof( FLT_REGISTRATION ), // Size
FLT_REGISTRATION_VERSION, // Version
0, // Flags
ContextRegistration, // Context Registration.
Callbacks, // Operation callbacks
ScannerUnload, // FilterUnload
ScannerInstanceSetup, // InstanceSetup
ScannerQueryTeardown, // InstanceQueryTeardown
NULL, // InstanceTeardownStart
NULL, // InstanceTeardownComplete
NULL, // GenerateFileName
NULL, // GenerateDestinationFileName
NULL // NormalizeNameComponent
};
Third member of FLT_REGISTRATION is an FLT_CONTEXT_REGISTRATION which define context type. And Callbacks is an FLT_OPERATION_REGISTRATION structure to register call back operator.Following is examples of this two structure.
const FLT_CONTEXT_REGISTRATION ContextRegistration[] = {
{ FLT_STREAMHANDLE_CONTEXT,
0,
NULL,
sizeof(SCANNER_STREAM_HANDLE_CONTEXT),
'chBS' },
{ FLT_CONTEXT_END }
};
[structure explain]
const FLT_OPERATION_REGISTRATION Callbacks[] = {
{ IRP_MJ_CREATE,
0,
ScannerPreCreate,
ScannerPostCreate},
{ IRP_MJ_CLEANUP,
0,
ScannerPreCleanup,
NULL},
{ IRP_MJ_WRITE,
0,
ScannerPreWrite,
NULL},
{ IRP_MJ_OPERATION_END}
};
[structure explain]
The most interesting part is ScannerPostCreate function.Then we move to ScannerPostCreate function and take a look.
This function check file extension then call ScannerpScanFileInUserMode function. If the return value safe, then we leave it for write check.Otherwise , use FltCancelFileOpen to cancel file open operator.
In function ScannerpScanFileInUserMode , it calls FltReadFile function to read file content to buffer then pass it to user space by FltSendMessage.And user space program is responsible for scanning the content.
[How to communicate between user space and kernel space]
HIT2012 Wargame Writeup : Binary 1
This writeup is about problem Binary 1 in HITCON 2012.
There is the description about Binary 1:
Kenny 意外地從探險家手上獲得了一張海外的藏寶圖,但看起來似乎失去了下半部分,你能幫助他找到寶藏嗎??
And there is a kenny.zip provided , which contain a Keyexe.jpge file inside.
We can observe that Keyexe.jpge can open by double-click , but can not open by image editor such as paint.So we can infer that Keyeze.jpge is not a jpge file but an exe file , which use windows reverse file name method to hind itself.[資料補充~~]
After change the file name to key.exe, we can open it by debugger(because origin filename include invalid character).
We can find out that jpge file showed is 2.jpge in temp directory. After short analyse , we can find out there are 3 files create while execution.Those files are 1.jpge,2.jpge and SYS. 1.jpge is an image file contain "ioctl: 6666" message.SYS is device driver. Now we can guess next step is to register this device and send 6666 message to it through IOCTL.
By using IDA or ollydbg , we can find device name is Kenny.Then we can write a small program to send message to driver.Then driver will response "Boracay.exe" in debug message. Finally we change the original executable's filename to Boracay.exe and execute it.The key "hey it nice" will displayed in DebugView.
[補充圖片]
ps. thanks for kost0911's sharing .He's article help me to find out device name , so I can complete this problem.
http://kost0911.pixnet.net/blog/post/91590907
There is the description about Binary 1:
Kenny 意外地從探險家手上獲得了一張海外的藏寶圖,但看起來似乎失去了下半部分,你能幫助他找到寶藏嗎??
And there is a kenny.zip provided , which contain a Keyexe.jpge file inside.
We can observe that Keyexe.jpge can open by double-click , but can not open by image editor such as paint.So we can infer that Keyeze.jpge is not a jpge file but an exe file , which use windows reverse file name method to hind itself.[資料補充~~]
After change the file name to key.exe, we can open it by debugger(because origin filename include invalid character).
We can find out that jpge file showed is 2.jpge in temp directory. After short analyse , we can find out there are 3 files create while execution.Those files are 1.jpge,2.jpge and SYS. 1.jpge is an image file contain "ioctl: 6666" message.SYS is device driver. Now we can guess next step is to register this device and send 6666 message to it through IOCTL.
By using IDA or ollydbg , we can find device name is Kenny.Then we can write a small program to send message to driver.Then driver will response "Boracay.exe" in debug message. Finally we change the original executable's filename to Boracay.exe and execute it.The key "hey it nice" will displayed in DebugView.
[補充圖片]
ps. thanks for kost0911's sharing .He's article help me to find out device name , so I can complete this problem.
http://kost0911.pixnet.net/blog/post/91590907
HIT2012 Wargame Writeup : Mobile 1
There was a new catalog - Mobile added in this year HIT wargame. Although there are two problem in this catalog , it can point out that mobile security is future trend in security.
Mobile 1 is an easy problem , there are only two things need to do.
First , unzip the apk file. Then open files one by one , then we can find some string in META-INF/CERT.RSA ."What is the guy's nickname in base64 format?" .So we can find the guy's nickname in article and encode it as base64 to get the key.
Reference to wiki , CERT.RSA is the certificate of the application
訂閱:
文章 (Atom)