In this problem, a pcap file is given and we are asked to find the target host of DDOS.
After list all ip sort by the packet number and trace it one by one, we can find most suspicious flow.
First is attack target to 109.123.118.42 which send a lot of GET connections.
Second one is target to 111.221.70.11, which is SYN Flood.
The third attack is targetting 199.7.48.190, which resend a lot of SYN with sequnce number 0.
The last one send a lot abnormal HTTP packet.
Combine this four address, the key is none_111.221.70.11_109.123.118.42_199.7.48.190_66.150.14.48
2013年7月8日 星期一
PHD CTF Quals 2012 Write Up: Forensic 100
In this problem, and QRcode image are given as following pic.
We first use online scanner to scan this QRcode and get the binary string.
After executing file, we get the string as output.
The first integer 328 may indicate the length of msg. Therefore we extract first 328 chars as a file, which is indeed an RAR file.
To extract RAR file, we need a password. Hence we use first string as password and express RAR file.
There is an secret.txt and key.
The key is 90f3910ff22f4be0dfa95a2fd6cb8a25
We first use online scanner to scan this QRcode and get the binary string.
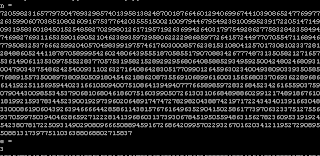
7F454C46010000000000000000004305020003001A0043051A00430504000000B931004305B220CD80252000010093CD803030343330354232323043443830323532303030303130303933434438300ASaving this string as a file, and using file command, we can recognized this file is an ELF executable.
After executing file, we get the string as output.
004305B220CD80252000010093CD80Then with stegsolve, we can extract some string.
328:5261 72211A07 00CE9973 80000D00 00000000 00001566 EFE453AE B7AFEBEB 515C366D 9C07555B 4739CBEE 3217360A 3A52E015 3C7AA47C F3BC9DEA 16A30B98 8B5ABCC2 B98BD56C 8E84EB4A 7CEACF43 74D01FD6 9D98C282 1D05B79B 2CC4D3E6 4CB09081 42566EEA C2862E0A 2BA7C559 7E7FCB77 97051CFE 55C8DF4A 10A93D07 2DC79C64 39C6E44D 9845B267 21A71566 EFE453AE B7AF74E5 062C467D BD49421B 47D68DB8 E7F5.
The first integer 328 may indicate the length of msg. Therefore we extract first 328 chars as a file, which is indeed an RAR file.
To extract RAR file, we need a password. Hence we use first string as password and express RAR file.
There is an secret.txt and key.
The key is 90f3910ff22f4be0dfa95a2fd6cb8a25
PlaidCTF 2012 Write Up: RSA 200
This problem is the second time which try to break RSA. In the previous practice, the reason to break RSA is using module already factored. In this problem, the vulnerability to break RSA is using small exponent number.
In this problem, an encrypted data is given with an public key.
Using RSA python module, we can find information about RSA algorithms.
(or use command: openssl rsa -pubin -in id-rsa.pub -text)
The exponent number used is 3, which is very small. And increasing the risk of rsa. Observing that the encrypt message is related small too, this give us a clue to solve rsa.
According to RSA encrypt schema, the formula below
So we wrote a program which use brute force to find K. To check if the 3-rd root of C-KN is an integer, we can find the true K and the key.
In this problem, an encrypted data is given with an public key.
Using RSA python module, we can find information about RSA algorithms.
(or use command: openssl rsa -pubin -in id-rsa.pub -text)
The exponent number used is 3, which is very small. And increasing the risk of rsa. Observing that the encrypt message is related small too, this give us a clue to solve rsa.
According to RSA encrypt schema, the formula below
It can reduce to
With e=3, we can get following formula
Since we have value of M and N, while C is plain text we need to solve, only K is unknown. With small small M and e, we can consider N is related small.So we wrote a program which use brute force to find K. To check if the 3-rd root of C-KN is an integer, we can find the true K and the key.
from Crypto.PublicKey import RSA
from Crypto.Util import asn1
from base64 import b64decode
import libnum
import math
import gmpy
pubkey = open('id-rsa.pub').read()
key = RSA.importKey(pubkey)
print "n = "
print key.publickey().n
print "e = "
print key.publickey().e
nkey = key.publickey().n
message = open("enc.dat",'r').read()
print libnum.s2n(message[:-1])
ct = libnum.s2n(message.rstrip())
print libnum.len_in_bits(ct)
c = ct
k = 1
while True:
if k % 10000 == 0 :
print k
p = gmpy.root(c, 3)[0]
if pow(p,3,nkey)==ct:
print libnum.n2s(p)
break
c += nkey
k+=1
2013年7月1日 星期一
ForbiddenBITS CTF 2013 Write Up : Misc 150 Invisible
In this problem, a file is provided. Dump the file, we can observe it only contain 0x20 and 0x09.
So we guess it is program call Whitespace. So we find the compiler and disassembler of Whitespace.
After executing the program, we get the following result.
We know that this program only accept some input. Then we disassemble the program and get it's instructions.
This program check if the first character is 'w' and second one is 's'. Then we collect the characters this program reads. And executes the program with expected input "wslang", the key will be shown.
So we guess it is program call Whitespace. So we find the compiler and disassembler of Whitespace.
After executing the program, we get the following result.
We know that this program only accept some input. Then we disassemble the program and get it's instructions.
This program check if the first character is 'w' and second one is 's'. Then we collect the characters this program reads. And executes the program with expected input "wslang", the key will be shown.
訂閱:
文章 (Atom)